Agam's Gecko


Sunday, March 29, 2009
MASSIVE CHINESE CYBER-SPY NETWORK UNCOVERED
 |
| R |
esearchers at the Canada-based Information Warfare Monitor, and at Cambridge University, UK, have uncovered an extensive and sophisticated cyber-espionage network operating from China, which has infiltrated Tibetan institutions in exile, as well as embassies and foreign ministries of over 100 countries. The main group of researchers, based at the University of Toronto's Munk Centre for International Studies, had been contacted after the computer security people at the Office of His Holiness the Dalai Lama suspected malicious intrusions almost two years ago.
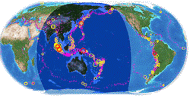
Based upon a malware program known as "gh0st RAT" — a Trojan which gives attackers complete, real-time control over an infected computer — the China-based network has been dubbed "GhostNet", and has infiltrated more than 1,200 computers belonging to diplomatic, political, economic and military targets. The network particularly focused on governments in South Asian and Southeast Asian countries. A comparison graphic shows a high penetration in this region, but targets were also found in North and South America, Europe and Africa.
 Asia is well-covered by China's Gh0st RAT thieves. Source: InfoWar Monitor |
The gh0st RAT software is remarkable in that, after it is secretly installed (by opening an infected email attachment or visiting a malicious website), the spies and thieves in China are able to operate the infected machine just like its own user. They can even switch on any web-cam present, enabling them to watch or listen to what the actual user is doing or saying.
Most of the servers controlling the network are based on Hainan Island in China, although one is located in southern California. The control interface is in Chinese. Evidence shows that information known to have been stolen by this network was immediately put to intimidating use by the Chinese government.
The Times contacted the Chinese consulate in New York for comment on these revelations, and the response was predictable.
"These are old stories and they are nonsense," the spokesman, Wenqi Gao, said. "The Chinese government is opposed to and strictly forbids any cybercrime."The two Cambridge researchers focused on the attacks against Tibetan organisations in exile, and concluded that they were designed "to collect actionable intelligence for use by the police and security services of a repressive state, with potentially fatal consequences for those exposed." Shishir Nagaraja and Ross Anderson have made their findings available in a freely downloadable report: "The snooping dragon: social-malware surveillance of the Tibetan movement".
The larger report by the Canadian researchers has been placed into the Scribd file-sharing site, but is downloadable only by registered members. However it does provide for embedding the documents, so here you go. It will be too small to read comfortably at this size, but just click the Full Screen Toggle on the right side of its tool-bar.
.










 Our way of saying "thanks" in the Thai way. Here a nak muay Thai (kickboxer) offers respect and thanks for his teacher (wai khru) before a match. This is our local variation on the ubiquitous "hat tip" used in general blog culture.
Our way of saying "thanks" in the Thai way. Here a nak muay Thai (kickboxer) offers respect and thanks for his teacher (wai khru) before a match. This is our local variation on the ubiquitous "hat tip" used in general blog culture.






